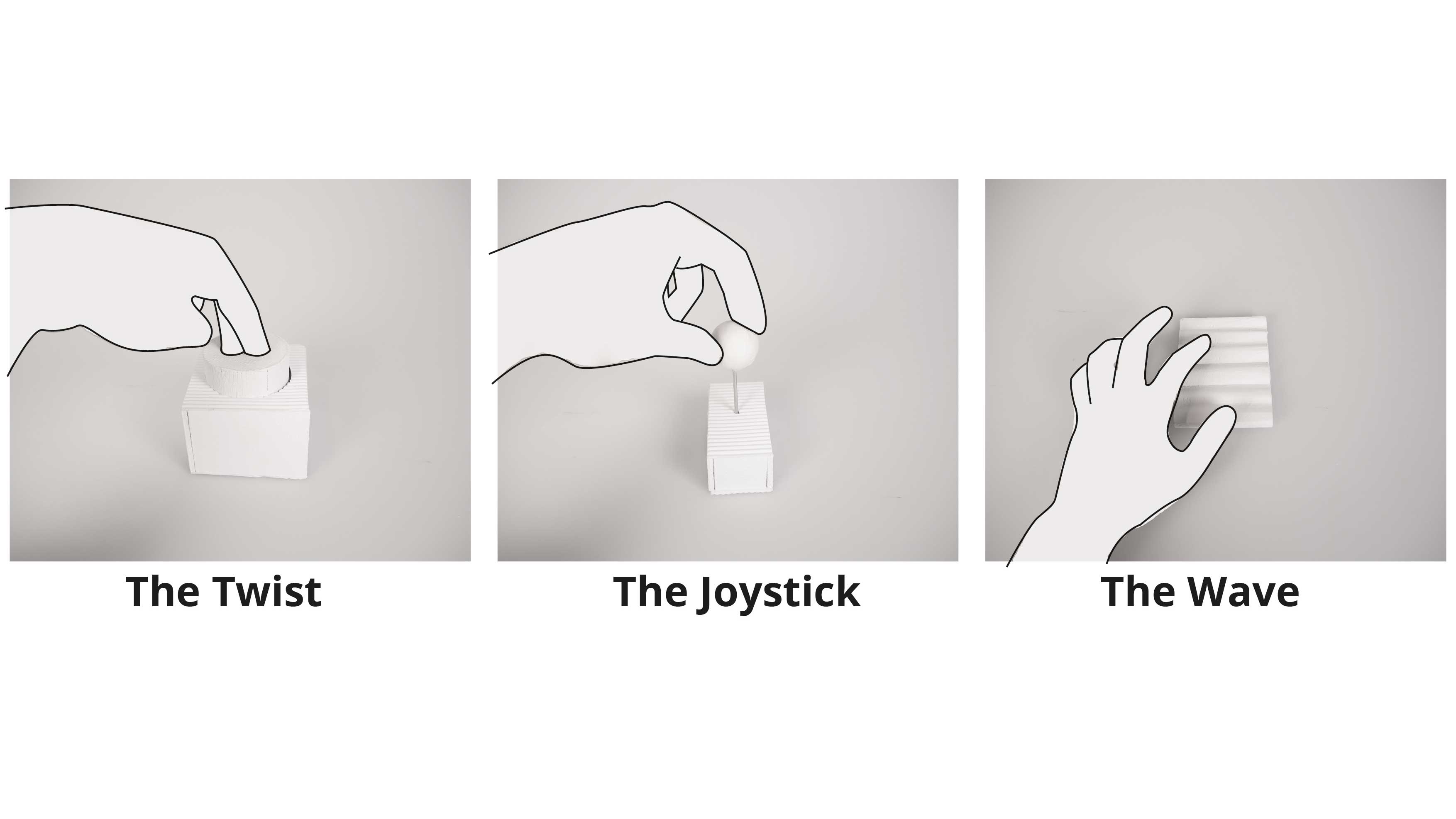
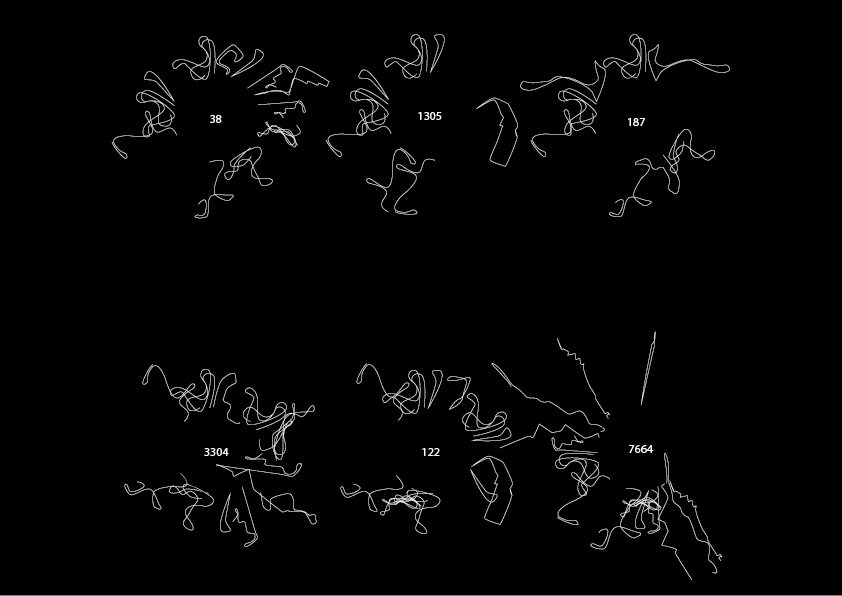
With the digitalisation of our world, passwords have become something which we encounter multiple times a day. Yet, we do not spend much attention to our passwords or care for them, which seems contradictory when thinking about their vital role. A reason for this is that passwords are not designed to be user friendly, it is almost impossible to create (enough) safe passwords and actually recall them. Therefore, this research explores how embodied interaction and muscle memory can be used for a password alternative. Through 6 experiments, this research tries to understand the movement space, the affordances, and the memorability aspects of an embodied password. Starting the research exploring how music conductors and music conductor students would express certain password qualities, this research gained insights to the movements which are suitable for a password. Using this movement space, the next step was to explore what the shape and the interaction of an embodied password had to be. Through 2 experiments, the basic shape of the password was found: a cylindrical object which reminded people of a combination lock. After this, an experiment was done with a 3x3 grid, in order to explore how the dimensions of the object would influence the perceived safety and the created passwords. This experiment resulted in the insights that the smaller objects were seen as safe, private, and quick. However, when people had to chose an object to use to enter a password, they often chose the middle sized object with a diameter of 60 mm and a height of 110 mm, as it fitted their hand perfectly. It therefore seems that there is a trade-off between safety and ergonomics. Therefore, the last experiment looked at the memorability aspect of an embodied password, using the 2 preferred artefacts. The memorability experiment lasted a week and showed that people can recall and reproduce their embodied passwords. Furthermore, insights were gained in the design elements of an embodied password, how people create and recall them, and the type of passwords created. The passwords were visualised with notation maps of the movements.
- Project 1 Year
- By Rosa van Koningsbruggen, Bart Hengeveld, Jason Alexander
- [1] Adams, A., & Sasse, A. (2005). Users are not the enemy: why users compromise security mechanisms and how to take remedial actions. Security and Usability, 639-649. [2] P. Inglesant and M. A. Sasse, “The True Cost of Unusable Password Policies: Password Use in the Wild,” p. 10.[3] B. AlFayyadh, P. Thorsheim, A. Jøsang, and H. Klevjer, “Improving Usability of Password Management with Standardized Password Policies,” p. 8. [4] Kuijer, L., Jong, A. D., & Eijk, D. V. (2013). Practices as a unit of design: An exploration of theoretical guidelines in a study on bathing. ACM Transactions on Computer-Human Interaction (TOCHI), 20(4), 21.